ISO / IEC 27001 is a widely used de-facto international security standard, which has grown in its popularity and adoption strongly in the recent years. Traditionally, it has been used by larger organizations, but it’s well suited for organizations of all sizes and types and, thus, the standard has spread more widely in recent years and it’s also used in smaller organizations. A specific driver in Europe recently has also been the GDPR, which imposes information security management requirements on both the controller and the processor. It is also often the case that the ISO 27001 standard and its binding controls are widely used as a basis for security requirements when contracts are made between a controller and a processor.
As a novelty, ISO / IEC 27701, which was recently published and is an extension to the ISO 27001 standard and includes not only information security but also privacy management. ISO 27701 is therefore an excellent option when you want to manage privacy with the same management system and when it is necessary to demonstrate the use of best practices in information security and compliance with privacy laws to third parties.
In addition, the compliance with the standards provides reassurance to management, employees, shareholders, authorities, customers and partners that information security and privacy is adequately managed, which often translates as a major competitive advantage during negotiations. The following describes in more detail the different aspects of the ISO 27001/27701 services offered by 2NS. These services, depending on the situation, can be used as independent or as a path in preparing for and maintaining certification.
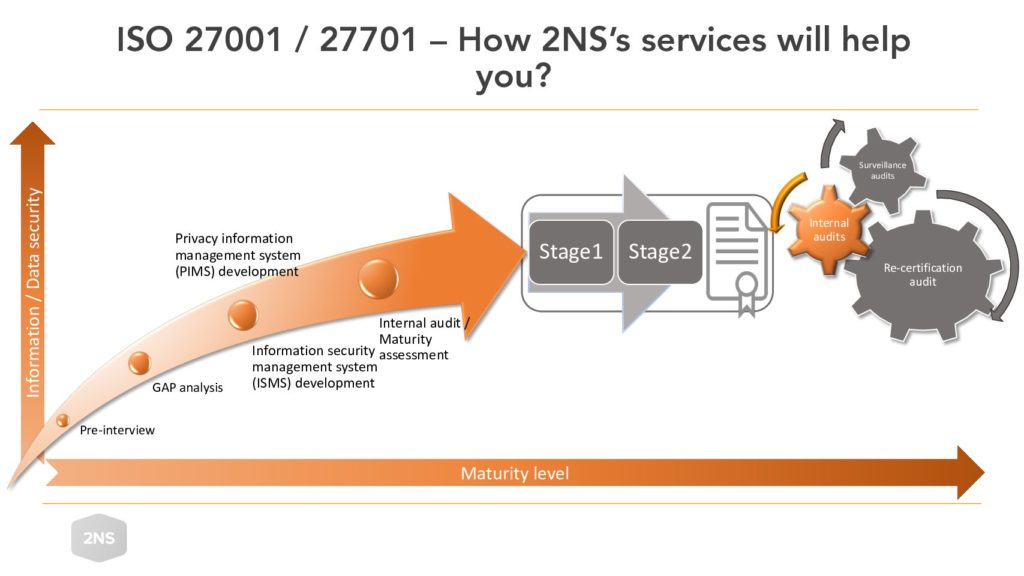
Pre-interview
The pre-interview examines the customer’s starting situation, organizational structure and operating environment. The aim of the pre-interview is to find out roughly the level of maturity (security / privacy management) the organization is at, what is being sought for and from which service it is worthwhile to start with. The pre-interview phase also gathers information on the issues that affect the next steps and, thus, also provides the readiness to estimate the project schedules, workloads and costs together with the customer.
Gap-analysis
The Gap analysis, as the name implies, analyses the current situation of information security/privacy and its possible current gaps. The gaps are identified by interviewing all aspects of the ISO 27001 or ISO 27701 standard, with the aim to provide information on the level of maturity in question against the chosen standard and produce a roadmap to support development. The gap analysis serves best in a situation where the starting position or degree of maturity is uncertain, you want an overall picture of the information security / privacy management situation and to identify the things that should be developed.
Development
The development phase of the Information Security Management System (ISMS) / Privacy Information Management System (PIMS) helps the customer to develop the identified gaps. Here, the customer can be helped on a project basis with various information security / privacy consulting, architecture and technical professional services. Our experts can be involved in, among other things, implementing, supporting or leading development, training and / or launching the management system itself. If necessary, our experts will also help you run the management system as a continuous CISO (Chief Information Security Officer) or DPO (Data Protection Officer) as a service. The use of professional services provides additional resources to development and, thus, also results can be gained much faster.
Internal audit / maturity assessment
The purpose of the internal audit / maturity assessment phase is to perform the impartial internal audit required by the certification and to determine the client’s readiness for the actual certification process. Because the audit must be objective and impartial, it is usually easiest to use an external audit partner. This step produces the required formal internal audit report and in addition as added value a statement of an independent audit and a roadmap for proposed development. The statement can be used in communication to third parties (such as existing or a prospect customer or partner) at a stage where ISO 27001 or ISO 27701 certification cannot yet be demonstrated. The roadmap proposal, on the other hand, in addition to the formal audit report, taking into consideration the business environment and risks, gives a more concrete picture of what development activities the customer should prioritize. This phase is well suited to a situation where the management system has been running and producing evidence of its operations for some time, you want to perform the internal audit required by the certification and assurance of the effectiveness is sought before applying for the certification.
Certification
The certification itself is carried out by an accredited certification body in two parts, where the first audit (Stage1) focuses on the certification readiness and the next step (Stage2) on the implementation of the management system. The audit covers all aspects of ISO 27001 or ISO 27701 and assesses the intent, implementation and effectiveness of the management system. Upon passing the audits, the client receives an ISO certificate, which demonstrates that it operates and manages information security (in the case of ISO 27001) or information security and privacy (in the case of ISO 27701) in accordance with the standard.
After the certification
ISO 27001 and ISO 27701 certificates are in principle valid for three years, during which time an accredited certification body carries out surveillance audits at least once a year (a total of at least three) of which the last is the so-called re-certification audit. This cycle is repeated every three years. One of the preconditions of ISO 27001 and ISO 27701 is also that objective and impartial internal audits must be carried out at planned intervals in the form of an audit program, including all requirements of ISO 27001 or ISO 27701 to be audited over a period of three years. This is also usually easiest to accomplish using a professional, impartial audit services provider partner.
Lasse Korvala
2NS Lead Security Consultant
CISSP, CISA, CISM, CRISC
