Red Teaming is a comprehensive security assessment in which 2NS utilizes real-world attacker tactics, techniques and procedures (TTPs) to evaluate target organization’s security. By emulating a realistic attack scenario, Red Teaming helps to identify weaknesses in the people, process and technologies used to defend the organization, and thus improves the organization’s capability to detect and react to security incidents.
Red Teaming projects are objective-based, and the goal is to emulate attacker’s actions in the target environment. The 2NS Red Team can utilize non-technical TTPs such as social engineering or even physical intrusion to meet the goals set for the project. The TTPs utilized in the project are selected based on the project’s goals, such as “Access server x containing business-critical data without alerting the organization’s cyber defense team“. 2NS Red Team follows the industry best practices and the latest threat information and research to emulate a realistic threat actor.
2NS also has experience in conducting Red Teaming projects using the TIBER-FI framework
Red Teaming attack:
- Simulates how real threat actors would approach your organization as a target
- Helps you asses what are the biggest risks and weakpoints in your security
- Is a good reminder about how complex combination of physical and cybersecurity actually is
Benefits of Red Teaming
- Proactively test organization’s response to a targeted attack.
- Validate effectiveness of security controls.
- Evaluate defense’s maturity level.
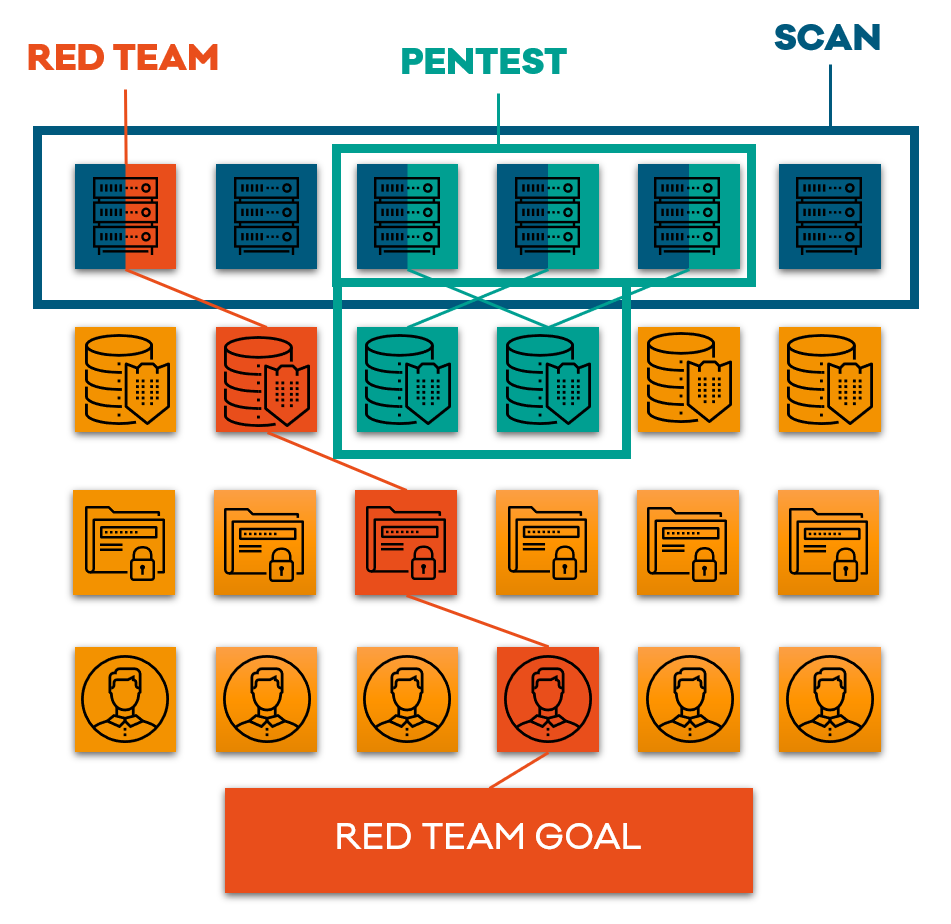
Red Teaming does not focus on discovering technical vulnerabilities in the target environment. However, vulnerabilities may be used to achieve certain goals set for the project. 2NS also provides services more-related to vulnerability discovery and assessment, such as Penetration Testing.
2NS provides the customer a detailed timeline of attacking events that can be correlated with SOC’s timeline to identify gaps in the security monitoring process.
2NS provides Red Teaming services using two main threat scenarios:
Full Engagement Model
2NS performs a complete, end-to-end Red Teaming engagement starting from OSINT and external reconnaissance where no initial access to the organization’s internal networks is provided. The full engagement model requires usually more time than assumed breach.
Assumed Compromise
In this model, an assumption is made that the simulated attacker has some level of access to the target at the start of the project. In this model, the attacker’s access can be simulated for example using a “stolen laptop”, by providing initial access password or by launching 2NS Red Team’s simulated malware that provides command and control.
Assumed compromise model can be performed in a shorter period of time than the end-to-end full engagement model.
How a Red Teaming project works?
- Project goals and methods are agreed with the customer
- Our team plans and executes the attacks based on information gathered and given
- Observations from attempted or successful attacks are gathered and reported to the customer

Read what our customers have to say
KEVA gains energy from a Red Teaming project
- “Keva wanted visibility into how its own observation skills and processes concerning information security worked in practice. Overall, the objective was to learn and develop its own information security.”
